Cybersecurity in 2024: facing new technological challenges
The cybersecurity It has become an essential priority for companies and individuals in the modern world. The cyber attacks are every time more sophisticated and can cause serious damage, from data loss to identity theft.
In this article, we are going to explore the trends that will shape the cybersecurity landscape in the coming years. These trends include the increase in sophistication of attacks the expansion of Internet of Things (IoT) and the development of new security technologies.
Increasing complexity of attacks
Cybercriminals are continually developing new methods to attack computer systems. For this new year, attacks are expected to be even more sophisticated, using advanced techniques such as deepfake he, stealth malware or the ransomware.
✓ Deepfake
He deepfake It is a technique of artificial intelligence which enables create fake videos or audios that look real. Cybercriminals could use this technique to spread false information or trick people into revealing sensitive information.
For example, a cybercriminal could create a deepfake of a company CEO giving instructions to transfer money to a bank account controlled by the cybercriminal.
Video Personalization Using Deepfake Technology
✓ Stealth malware
He stealth malware is a type of malware that is designed to avoid being detected by security systems. Cybercriminals could use this type of malware to steal data or install backdoors into computer systems.
For example, a cybercriminal could use stealth malware to steal credit card data from a bank’s customers.
New zero-click hack targets iOS users with stealthy malware with root privileges
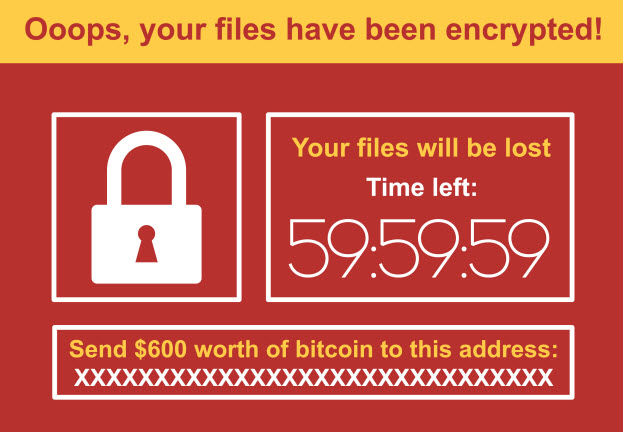
✓ Ransomware
He ransomware It is a type of malware that encrypts the victim’s data and demands a ransom to decrypt it. Cybercriminals could use this type of malware to extort companies or individuals.
For example, a cybercriminal could use ransomware to encrypt a company’s data and demand a million-dollar ransom.
How to act in the event of a ransomware attack
Other examples of sophisticated attacks
In addition to these techniques, cybercriminals also use other sophisticated attacks, such as:
- Supply chain attacks– Cybercriminals attack a company’s suppliers to gain access to the company’s computer systems.
- Phishing attacks– Malicious actors send fraudulent emails or text messages that attempt to trick users into revealing sensitive information.
- Denial of Service (DoS) Attacks– Attackers overload a computer system with network traffic to make it inaccessible.
Tips to protect yourself from sophisticated attacks
To protect themselves from sophisticated attacks, companies and individuals should take the following steps:
- Implement strong security policies: Security policies must define the procedures that must be followed to protect information and computer systems. These policies should cover all aspects of security, from password management to mobile device use.
- Train employees in cybersecurity– Employees should be trained on the latest cyber threats and how to protect themselves from them. Training must be continuous so that employees are up to date with the latest trends.
- Use the latest security technologies– Advanced security technologies can help protect businesses and individuals from cyber attacks. These technologies must be implemented and maintained properly.
The expansion of the Internet of Things (IoT)
He IoT is a network of devices connected to the Internet that can collect and share data. By 2024, it is expected that there will be more than 45 billion of devices connected to the Internet, which will create a much larger attack surface for cybercriminals.
IoT devices are usually more vulnerable to attacks than traditional computers. This is because they usually have fewer security resources since They are designed to be easy to use.
Cybercriminals could take advantage of the expansion of the IoT to attack the computer systems of companies and individuals. For example, they could use IoT devices to steal data or launch denial-of-service attacks.
The expansion of IoT can be seen in the following examples:
- home automation– Smart home devices such as smart thermostats, security cameras, and smart locks are becoming increasingly popular. These devices can be controlled remotely from a smartphone or tablet.
- The industry– Internet-connected industrial devices such as sensors and controllers are used to automate industrial processes. These devices can collect data on the performance of equipment and processes.
- Transport: Internet-connected vehicles, such as self-driving cars, use sensors and software to collect data about the environment. This data can be used to improve transportation safety and efficiency.
Tips to protect IoT devices
To protect IoT devices from attacks, organizations and users should implement the following actions:
- Update device firmware: Firmware is the software that controls the operation of IoT devices. Firmware updates usually include security fixes.
- Use strong passwords: These must be long, complex and subject to periodic changes to ensure greater security.
- Use two-factor authentication (2FA): 2FA adds an extra layer of security by requiring users to enter a verification code in addition to their password.
- Use firewall– A firewall can help block unauthorized access to IoT devices.
The development of new security technologies
Companies and individuals are developing new security technologies to protect against cyber attacks. In the coming years, these technologies are expected to develop further and become an essential part of cybersecurity.
Some of the new security technologies being developed include:
✓ Artificial intelligence
The artificial intelligence It can be used to detect cyber threats that traditional security systems cannot detect. For example, artificial intelligence can be used to analyze network traffic for suspicious patterns or for identify new malware.
For reference, the company Proofpoint uses artificial intelligence to analyze incoming emails for suspicious patterns, such as links to malicious websites or infected attachments.
✓ Quantum computing
The quantum computing could be used to develop new security algorithms that are more secure than current algorithms. Quantum algorithms can break traditional security algorithms in a relatively short time.
As an example, the company IBM is developing a new encryption algorithm that is resistant to quantum attacks.
✓ Biometric cybersecurity
The biometric cybersecurity uses biological characteristics, such as fingerprints or facial recognition, to authenticate users. Biometric cybersecurity is more difficult to hack than traditional passwords.
By way of illustration, the society Manzana uses facial recognition to authenticate your iPhone users.
Reflections
The cybersecurity landscape in 2024 will be a challenging environment. Cyberattacks will become increasingly sophisticated and the attack surface will become much larger.
Organizations and individuals should adopt advanced security measures to protect yourself from cyber attacks. These measures should include the implementation of strong security policies the employee training regarding cybersecurity and use of the latest security technologies.